For utilities, GIS is no longer just an internal back-office tool…it is a mission-critical system used by field crews, engineers, contractors, and even public safety partners. Since ArcGIS Enterprise is a mission-critical system for web and mobile GIS, the question arises: how do you make it accessible to both your internal employees and external contractors without compromising security or creating a nightmare for IT?
One option to solve this problem is…split DNS.
What is Split DNS and Why Might it be Needed?
Split DNS is a Domain Name System (DNS) configuration that allows the same fully qualified domain name (FQDN) to resolve different IP addresses depending on whether a user is connecting from inside or outside your network.
In the simplest terms, Internal users (employees on the corporate network or VPN) see the internal IP address for ArcGIS Enterprise. External users (contractors, partners, or employees working remotely without VPN) see the public IP address for ArcGIS Enterprise.
The hostname (e.g., gis.utilityname.com) is the same for everyone. The “split” happens in DNS, not in the URL.
What are the benefits of this approach? The challenge occurs in the entry point of your users of ArcGIS Enterprise. Utilities often have a mixed audience of ArcGIS Enterprise users. Internal employees in engineering, asset management, operations, field services, etc. External contractors performing construction, inspection, vegetation management, or emergency response work.
Without split DNS, utilities typically face two options:
- Two separate URLs—one for internal and one for external users.
- Force all users to come through a single public entry point, even if they are on the internal network.
Both approaches have downsides and can lead to confusion for end users, increased security exposure, or unnecessary internet routing for internal traffic. Split DNS solves these issues by:
- Maintaining a single URL for all users.
- Routing internal traffic entirely within your network for faster performance.
- Allowing external users to connect securely without VPN in some configurations.
- Simplifying mobile workflows where field devices roam between inside and outside networks.
So How Does Split DNS Work?
A split DNS setup for ArcGIS Enterprise typically looks like this:
- Single DNS name for ArcGIS Enterprise Portal and services—for example:
- gis.utilityname.com
- Internal DNS zone (inside corporate network):
- gis.utilityname.com resolves to an internal load balancer or reverse proxy pointing to the ArcGIS Enterprise servers in the DMZ or internal network.
- External DNS zone (public internet):
- gis.utilityname.com resolves to a public IP address on a load balancer or reverse proxy that routes traffic to ArcGIS Enterprise through a DMZ.
- Certificates and HTTPS:
- Both internal and external DNS entries use the same SSL certificate so that the browser or mobile app sees the connection as secure and trusted.
- Authentication:
- Utilities often configure SAML or OIDC single sign-on so that both internal and external users authenticate through the same identity provider (with role-based access controlling who sees what).
What is Happening Behind the Scenes?
When an internal employee opens a browser or Field Maps app and enters gis.utilityname.com, their device queries the internal DNS server, which responds with the internal IP address. The request never leaves the corporate network.
When an external contractor does the same, their device queries a public DNS server (usually from their ISP or mobile carrier). That server returns the public IP address, which points to a utility-managed secure entry point (often in the DMZ or cloud). The load balancer or reverse proxy handles authentication and routes the traffic to the ArcGIS Enterprise environment.
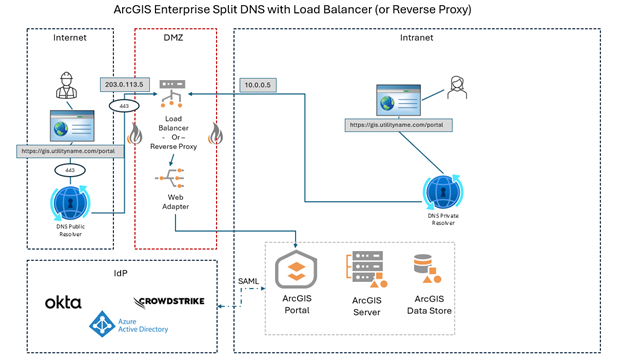
The magic is that both users type the same URL—the DNS server decides which IP they get.
Best Practices to Consider
Following best practices when implementing split DNS for ArcGIS Enterprise is critical for utilities because these guidelines ensure the system is secure, dependable, and user-friendly. Adhering to recommended security measures such as routing all external traffic through a load balancer or reverse proxy with TLS encryption, protects sensitive infrastructure data from unauthorized access. Using a single, consistent DNS name simplifies access for both internal staff and contractors, reducing confusion and training needs, while proper role-based access control ensures users only see the data and tools they need. Coordinating closely between GIS, IT, and security teams ensures architecture decisions align with corporate policies, compliance requirements, and performance goals. Testing roaming scenarios for field devices guarantees a seamless user experience whether users are on internal networks or public cellular connections. By embedding these best practices into the design, deployment, and ongoing maintenance of ArcGIS Enterprise, utilities can deliver a high-performing GIS platform that meets operational demands without sacrificing security or usability.
Additionally, here are some more specific best practices for setting up split DNS:
- Use a Consistent DNS Name. Pick a clear and memorable FQDN for ArcGIS Enterprise and avoid using server hostnames. Example: gis.utilityname.com instead of gisprtsx01.utilityname.corp.local.
- Secure the Perimeter. Ensure external access is routed through a secure reverse proxy, with web application firewall (WAF) features if possible.
- Implement Role-Based Access Control. Limit what external contractors can see and edit. This is critical for protecting sensitive infrastructure data. For ArcGIS Portal, this can normally be achieved with Groups.
- Assess Roaming Scenarios. Many field devices move between internal Wi-Fi and public cellular networks. Make sure authentication and DNS resolution work seamlessly without requiring the user to log in twice.
- Coordinate Between GIS and IT. Successful split DNS requires close collaboration between GIS administrators, network engineers, and security teams.
Conclusion
Utilities operate critical infrastructure, so balancing security and accessibility is essential. Split DNS allows a single, secure ArcGIS Enterprise environment to serve both internal employees and trusted external partners—without maintaining two separate systems.
For utilities, this means:
- Contractors can access maps and data from the field without complicated VPN setups.
- Internal workflows stay fast and secure on the corporate network.
- Users have consistent experience whether they are in the office, at a job site, or responding to an emergency.
When implemented correctly, split DNS is a low-friction, high-impact technology that supports collaboration, efficiency, and security for modern utility GIS operations.

What do you think?